 Anonforce
Anonforce
boot2root machine for FIT and bsides guatemala CTF
Overview
Anonforce is on the easier side of the rooms that I have done. It will display how to exploit FTP, how to use hashcat and gpg2john.
Recon
nmap -vv -sV -Pn <Target IP>
FTP exploit
It is common for FTP to allow anonymous login so I immediately check to see if we can login anonymously.
ftp anonymous@<Target IP>
From here I check to see what users we have in the /home directory
cd /home
ls -al
I can see we have a melodias user after listing their files we can see we have the user.txt file.
mget /home/melodias/user.txt and we have our first flag.
I return to the root directory with cd / run ls -al and see a file called notread that isn't normally within this directory.
mget private.asc backup.pgp
PGP Files
The private.asc file is a key for the backup.pgp file. After some research into gpg files I came across this. I try to directly import the private.asc key but fails since I don't have the passphrase.
gpg --import private.asc
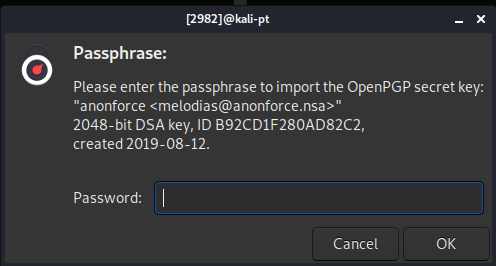
So I will have to use gpg2john to get the passphrase.
gpg2john
gpg2john will convert the asc format to a format that john can understand.
gpg2john ../private.asc > ../<File_name_you_want
Now run john on that file you just made to crack it.
We have the passphrase so run gpg --import private.asc
Once the key is imported decrypt the backup.pgp file
gpg --decrypt backup.pgp
Backup.pgp
From the contents of the backup.pgp file, we can gather that it is the shadow file of the system. Which contains the password hashes for all the accounts, within it we can find the password hash for the root account. We can copy this hash to a file and have john decrypt it for us, we know the type of hash from the $6$ at the beginning of the hash. You can learn more here.
Root.txt
Now that we have the root password all we have to do is SSH into the system and locate the root flag.
SSH root@<Target IP>
No comments:
Post a Comment